
Malware Analysis using Wireshark
RedLine Stealer is among the most widespread and prevalent information-stealing malware logs. It is commonly disseminated via phishing emails, malicious websites, or bundled with software. Once it infiltrates a system, RedLine can extract a variety of sensitive data, including passwords, credit card details, cryptocurrency wallet seed phrases, cookies, and application data. Additionally, it can gather information about the system itself, such as the operating system version, active processes, and installed antivirus programs.In this lab, with data provided by malware-traffic-analysis.net, network traffic from an Active Directory environment has been captured. By utilizing Wireshark, I can perform a thorough packet capture analysis to examine the malware infection. The LAN details are as follows:
- LAN segment range: 10.7.10.0/24
- Domain: coolweathercoat.com
- Domain controller IP address: 10.7.10.9

Before delving into the packet details, I can obtain an overview of the pcap file by examining the Protocol Hierarchy under the Statistics tab. This offers a summary of the different protocols present in the traffic and their respective percentages. This method can swiftly highlight anomalies, such as an unusually high volume of HTTP traffic.


Additionally, from the Statistics tab, I can compile a summary of all the conversations that occurred within the traffic. This is useful for identifying all endpoints and understanding the flow of traffic. The summary for this specific pcap indicates that all traffic is associated with the IP address 10.7.10.47.

Additionally, from the Statistics tab, I can compile a summary of all the conversations that occurred within the traffic. This is useful for identifying all endpoints and understanding the flow of traffic. The summary for this specific pcap indicates that all traffic is associated with the IP address 10.7.10.47.

To further investigate, I examine the TCP stream by right-clicking on the first HTTP GET request packet and selecting “Follow” -> “TCP Stream”.

The GET requests to 623start[.]site indicate that they were initiated from Windows PowerShell, as evidenced by the user-agent details. The first traffic request resulted in an HTTP response code 404 (not found) error from the Apache server. It seems that Windows Defender antivirus intercepted and blocked the outgoing traffic to this site. The second request also returned a 404 error for a URL related to an install status, likely intended to inject malware onto the victim’s system.

The third HTTP GET request to hxxp://guiatelefonos[.]com/data/czx.jpg returned an HTTP 301 error code, indicating a redirection. This redirection was to HTTPS, as evidenced by the traffic being sent over port 443.


Both sites have been flagged by numerous security vendors as malicious domains associated with malware distribution. Specifically, the “guiatelefonos” URL has been identified as being used by REDLINE.

Returning to the pcap, I continue to follow this TCP stream and discover incoming command-and-control (C2) traffic directed at the victim from the IP address 194.26.135.119 on port 12432. To narrow down the analysis, I focus specifically on the incoming traffic from the C2 server to the victim.


This data reveals that the user profile was searched in both the Desktop and Documents folders for keywords such as *.txt, *.doc, key, wallet, and seed to locate cryptocurrency private keys.

Scrolling down further, the data shows that the malware searched for specific cryptocurrency wallets such as Metamask, BinanceChain, and Phantom. External system analysis indicates that information was gathered and transmitted.

Additionally, the malware scanned the victim’s AppData directory for various applications such as Brave Software, Google, Microsoft Edge, NVIDIA, Steam, and Mozilla, among others.

Lastly, the malware also targeted private API keys and login credentials for services such as Facebook, Amazon AWS, Azure, Docker, Okta, Slack, and others.

To examine the outgoing traffic from the victim to the C2 server, I will reverse the stream.
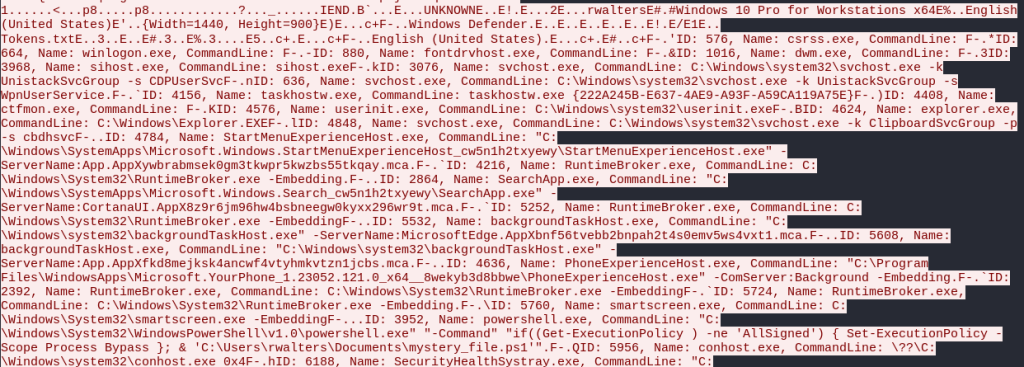
At the end of the packet, there are indicators of compromise. First, there is a list of all the running processes on the victim’s Windows 10 system.
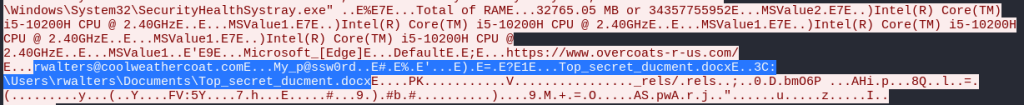
Lastly, for the report, the victim can be further identified by their MAC address, hostname, and user account name. Since I have already determined that this is a Windows host, I can use NBNS traffic to identify the hostname. NBNS (NetBIOS Name Service) is a Microsoft TCP/IP protocol used for networking on a LAN segment for file and printer sharing. Applying “nbns” as the search filter returns the following NBNS packets from the victim at 10.7.10.47 to the LAN broadcast at 10.7.10.255, revealing the hostname DESKTOP-9PEA63H. The Ethernet details include the user’s MAC address: 80:86:5b:ab:1e:c4.
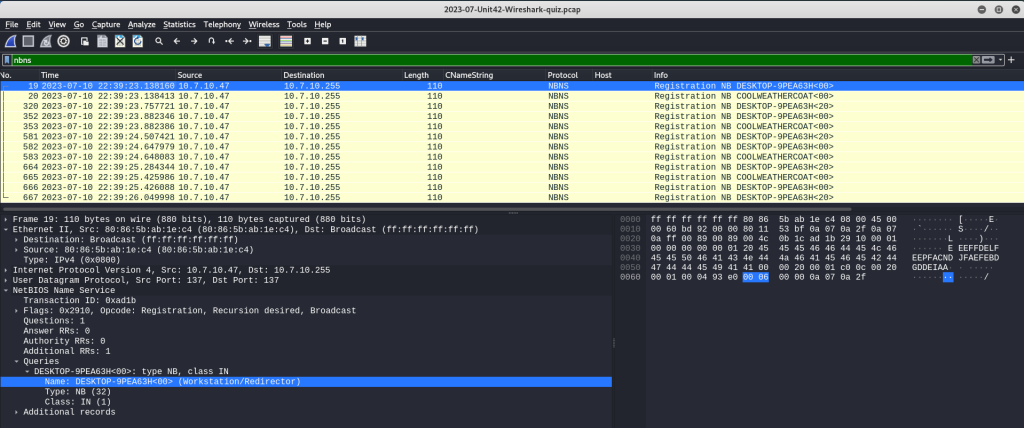
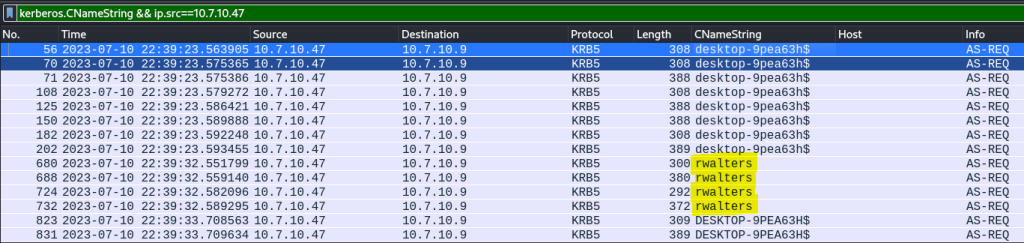
The Windows user account name can be identified using Kerberos traffic. Kerberos is the protocol used for authenticating service requests between hosts on an unsecured network and is the default authorization method in Microsoft Windows. I will apply “kerberos.CNameString” as a search filter along with the victim’s IP address.
Dissecting a RedLine Malware Infection: A Forensic Deep Dive
In the ever-evolving landscape of cyber threats, malware actors are constantly refining their tactics to evade detection and maximize their illicit gains. This investigation provided a firsthand look into the inner workings of a RedLine Stealer infection, shedding light on the meticulous methods employed by these nefarious actors.Through a comprehensive analysis of the network traffic captured in an Active Directory environment, we unraveled a chilling narrative of how RedLine Stealer operates. The malware, known for its prolific distribution through phishing emails, malicious websites, and software bundles, managed to infiltrate the victim’s system, setting the stage for a calculated data exfiltration operation.The initial signs of compromise manifested in the form of unencrypted HTTP GET requests originating from the victim’s IP address, a telltale red flag in the cybersecurity realm. These requests, directed towards suspicious domains flagged by multiple security vendors as malware distribution points, were the first indicators of the impending attack.As the investigation progressed, we uncovered a command-and-control (C2) channel established between the victim’s machine and a remote server, facilitating the bidirectional flow of malicious instructions and stolen data. The malware’s insidious tentacles reached deep into the victim’s system, meticulously scouring user profiles, desktop folders, and document directories for sensitive information.With surgical precision, RedLine Stealer targeted cryptocurrency wallets, private keys, and seed phrases, leaving no stone unturned in its quest for financial gain. The malware’s voracious appetite extended beyond digital currencies, as it scoured the victim’s AppData directory for a plethora of applications, including web browsers, gaming platforms, and productivity suites.Perhaps most alarmingly, the malware sought to compromise the victim’s digital identity by harvesting private API keys and login credentials for a multitude of services, ranging from social media platforms to cloud computing providers and enterprise authentication solutions.As the investigation drew to a close, we were able to piece together a comprehensive picture of the victim’s system, including running processes, MAC address, hostname, and user account name. These indicators of compromise serve as invaluable resources for incident response teams and security professionals, enabling them to fortify their defenses and mitigate the risk of future attacks.In summary, this investigation underscored the grave threat posed by RedLine Stealer and its ilk, highlighting the importance of robust cybersecurity measures, including regular software updates, strong password management, and comprehensive employee training. Only through a multi-layered approach can organizations hope to safeguard their digital assets and maintain the trust of their stakeholders in an increasingly perilous cyber landscape.


